In today’s hyper-connected world, where data reigns supreme and digital interactions are the lifeblood of commerce and communication, cybersecurity is no longer a luxury—it’s a fundamental necessity. From the individual navigating online banking to multinational corporations managing vast data networks, the threat landscape is constantly evolving, demanding ever-more sophisticated defenses. This isn’t just about preventing data breaches; it’s about safeguarding reputations, maintaining trust, and ensuring the smooth functioning of our increasingly digital lives.
The stakes are higher than ever before, making the growing importance of cybersecurity undeniable.
This escalating threat necessitates a multi-pronged approach, encompassing robust technological solutions, stringent regulatory compliance, and a proactive, well-trained workforce. Understanding the complexities of modern cyberattacks, adapting to the shift towards remote work, and cultivating a culture of security awareness are crucial steps in mitigating risks and building a resilient digital future.
The Evolving Threat Landscape
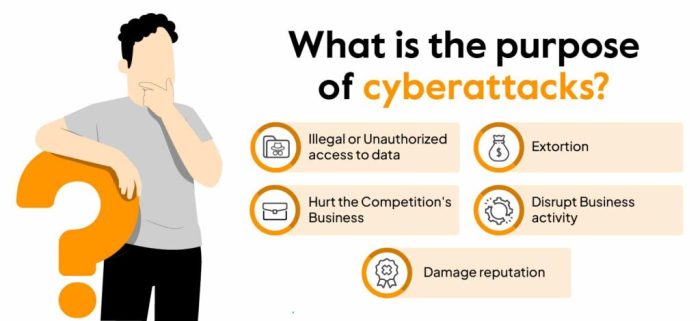
The digital world, while offering unprecedented opportunities, has also become a breeding ground for increasingly sophisticated cyber threats. Individuals and organizations alike face a constantly shifting landscape of risks, demanding proactive and adaptive security measures. The sheer volume and complexity of these threats necessitate a comprehensive understanding of their nature and impact to effectively mitigate the potential damage.
The sophistication of cyberattacks has evolved dramatically. Early attacks were often opportunistic and relatively simple, targeting easily exploitable vulnerabilities. Today, however, attackers leverage advanced techniques like artificial intelligence, machine learning, and automation to launch highly targeted and complex campaigns. These attacks often involve multiple vectors and exploit zero-day vulnerabilities, making them exceptionally difficult to detect and defend against. This evolution necessitates a shift from purely reactive security measures to proactive strategies that anticipate and preempt attacks.
Major Cyber Threats and Mitigation Strategies
Understanding the various types of cyber threats is crucial for developing effective security strategies. The following table categorizes common threats, highlighting their targets, potential impacts, and recommended mitigation approaches.
| Threat Type | Target | Impact | Mitigation Strategies |
|---|---|---|---|
| Malware (viruses, ransomware, spyware) | Individual computers, networks, servers | Data loss, system disruption, financial loss, reputational damage | Antivirus software, regular software updates, strong passwords, employee training, data backups |
| Phishing and Social Engineering | Individuals, organizations | Credential theft, malware infections, data breaches, financial fraud | Security awareness training, multi-factor authentication, email filtering, robust password policies |
| Denial-of-Service (DoS) Attacks | Websites, online services | Service unavailability, loss of revenue, reputational damage | Redundant infrastructure, DDoS mitigation services, network security monitoring |
| Data Breaches | Databases, cloud storage, individual accounts | Data loss, identity theft, financial loss, regulatory fines, reputational damage | Data encryption, access control, intrusion detection systems, incident response planning |
| Insider Threats | Organizations | Data theft, sabotage, system compromise | Background checks, access control policies, employee monitoring, security awareness training |
| Supply Chain Attacks | Organizations and their suppliers | Compromised systems, data breaches, disruption of operations | Vendor risk management, secure software development practices, thorough vetting of suppliers |
Examples of High-Profile Cyberattacks
Several recent high-profile cyberattacks highlight the devastating consequences of sophisticated cybercrime. Analyzing these incidents provides valuable insights into the evolving threat landscape and the need for robust security measures.
The 2020 SolarWinds supply chain attack, for example, demonstrated the potential for widespread damage when attackers compromise a trusted software provider. Thousands of organizations were affected, highlighting the vulnerability of supply chains and the need for rigorous security practices throughout the entire ecosystem. Similarly, the Colonial Pipeline ransomware attack in 2021 caused significant fuel shortages, underscoring the real-world impact of cyberattacks on critical infrastructure.
These attacks underscore the need for proactive security measures, robust incident response plans, and a strong focus on supply chain security.
The Rise of Remote Work and its Security Implications
The dramatic shift towards remote work, accelerated by recent global events, has fundamentally reshaped the modern workplace. While offering flexibility and increased productivity for many, this paradigm shift has also significantly expanded the attack surface for cybercriminals. The decentralized nature of remote workforces presents unique security challenges that require a proactive and multi-faceted approach. Understanding these risks and implementing robust security measures is no longer optional; it’s critical for business continuity and data protection.The increased reliance on personal devices, home networks, and cloud services introduces vulnerabilities previously less prevalent in traditional office environments.
Employees working from various locations, using diverse internet connections and potentially unsecured networks, expose organizations to a wider range of threats, from phishing attacks and malware infections to data breaches and insider threats. The lack of centralized IT control and the difficulty in consistently enforcing security policies further exacerbate these risks.
Security Risks Associated with Remote Work Environments
Remote work environments introduce a broader spectrum of security risks compared to traditional office setups. These risks stem from the dispersed nature of the workforce, increased reliance on personal devices, and the challenges in maintaining consistent security protocols across diverse locations and network configurations. For example, an employee working from a coffee shop using public Wi-Fi is significantly more vulnerable to man-in-the-middle attacks than an employee connected to a secure corporate network within a controlled office environment.
Similarly, the use of unpatched personal devices increases the likelihood of malware infections, potentially compromising sensitive company data. Furthermore, the lack of physical security controls in home offices makes devices more susceptible to theft or unauthorized access. The blurred lines between personal and professional life in a remote work setting also increase the risk of accidental data exposure or unintentional breaches of security policies.
These risks highlight the critical need for robust security measures tailored to the unique challenges of a remote workforce.
Best Practices for Securing Remote Work Setups
Implementing a comprehensive security strategy for remote work requires a multi-layered approach encompassing device security, network security, and data protection.
Prior to outlining specific best practices, it is crucial to understand that a robust security posture is built upon a foundation of strong security awareness training for all employees. Regular training sessions should cover topics such as phishing awareness, password management, and secure communication practices.
- Device Security: Enforce the use of company-provided or approved devices, equipped with up-to-date anti-malware software and strong encryption. Implement device management solutions to remotely monitor and control devices, ensuring compliance with security policies. Require strong passwords or multi-factor authentication for all devices and accounts. Regularly update operating systems and applications.
- Network Security: Encourage the use of secure VPN connections to encrypt data transmitted between remote devices and company networks. Educate employees about the risks of using public Wi-Fi and advise them to avoid accessing sensitive data on unsecured networks. Implement network segmentation to isolate sensitive data and applications from less critical systems.
- Data Protection: Implement robust data loss prevention (DLP) measures to prevent sensitive data from leaving the company network. Enforce data encryption both in transit and at rest. Establish clear data handling policies and procedures for remote workers, including guidelines for data storage, sharing, and disposal.
Comparison of Security Challenges: Remote vs. Traditional Office Environments
While traditional office environments have their own security vulnerabilities, the challenges presented by remote work are qualitatively different. In a traditional office, physical security controls such as access cards, security cameras, and on-site IT support provide a degree of protection. Network security is typically more centralized and easier to manage. Remote work, however, decentralizes the security perimeter, extending it to potentially unsecured home networks and personal devices.
This expansion significantly increases the attack surface and complicates security management. The lack of direct oversight and the difficulty in enforcing security policies consistently across diverse locations and devices further amplify the security risks associated with remote work. The reliance on diverse internet connections and the potential for employees to use unpatched personal devices adds another layer of complexity.
Effectively addressing these challenges requires a strategic shift towards a more proactive and adaptable security approach, emphasizing employee training, robust security technologies, and continuous monitoring.
Data Privacy and Security Regulations
The digital age has ushered in an era of unprecedented data collection, creating both immense opportunities and significant risks. Individuals are increasingly concerned about how their personal information is used, leading to a surge in data privacy regulations globally. These regulations aim to protect individuals’ rights and hold organizations accountable for the security and responsible handling of personal data.
Understanding these regulations and their implications is paramount for businesses operating in today’s interconnected world.The landscape of data privacy is complex and constantly evolving, but several key regulations have established global standards. These regulations impose significant obligations on organizations, impacting how they collect, store, process, and share personal data. Failure to comply can result in substantial financial penalties and reputational damage, undermining trust and potentially jeopardizing business operations.
Key Data Privacy Regulations and Their Impact
The General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in California are two prominent examples of comprehensive data privacy laws. GDPR applies to any organization processing personal data of EU residents, regardless of the organization’s location. CCPA, while geographically limited, has served as a model for other state-level privacy laws and highlights a growing trend toward stricter data protection measures in the United States.
Both regulations grant individuals greater control over their personal data, including the right to access, correct, delete, and restrict the processing of their information. They also impose stringent requirements on organizations regarding data security, breach notification, and data protection impact assessments. The impact on organizations includes increased costs associated with compliance, the need for robust data security measures, and the implementation of new data governance processes.
Companies must invest in technology and personnel to ensure adherence to these regulations, demonstrating a tangible shift in how organizations approach data management.
Penalties for Non-Compliance
Non-compliance with data privacy regulations can lead to severe consequences. GDPR, for example, imposes substantial fines of up to €20 million or 4% of annual global turnover, whichever is higher. CCPA penalties, while lower, can still reach significant amounts. Beyond financial penalties, non-compliance can damage an organization’s reputation, leading to loss of customer trust, decreased brand value, and potential legal challenges.
The reputational damage alone can outweigh the financial penalties, creating a significant incentive for organizations to prioritize compliance. For instance, a major data breach resulting from inadequate security measures can severely damage a company’s reputation, even if the financial penalties are relatively low.
Steps to Ensure Compliance
Organizations can take several proactive steps to ensure compliance with data privacy regulations:
- Conduct regular data protection impact assessments (DPIAs) to identify and mitigate potential risks.
- Implement robust data security measures, including encryption, access controls, and regular security audits.
- Develop clear and concise privacy policies that are easily accessible to individuals.
- Provide individuals with transparent and meaningful control over their personal data, including the ability to access, correct, and delete their information.
- Establish data breach response plans to effectively manage and mitigate the impact of potential breaches.
- Train employees on data privacy and security best practices.
- Appoint a data protection officer (DPO) to oversee compliance efforts (where required).
- Maintain comprehensive records of data processing activities.
- Engage in ongoing monitoring and review of compliance measures to adapt to evolving regulations and threats.
The Importance of Cybersecurity Awareness Training
In today’s interconnected world, the human element remains the weakest link in the cybersecurity chain. Sophisticated firewalls and robust encryption protocols are rendered useless if employees fall prey to cleverly crafted attacks. A comprehensive cybersecurity awareness training program is no longer a luxury; it’s a critical necessity for any organization, regardless of size or industry. Investing in training empowers employees to become the first line of defense, significantly reducing the risk of breaches and data loss.A robust cybersecurity awareness training program should be multifaceted, engaging, and regularly updated to reflect the ever-evolving threat landscape.
Effective training doesn’t just involve passively listening to lectures; it requires active participation and reinforcement to truly embed security best practices into employees’ daily routines. The goal is to foster a security-conscious culture where employees understand their role in protecting sensitive information and proactively report suspicious activity.
Key Elements of a Comprehensive Cybersecurity Awareness Training Program
A successful training program incorporates various learning methods to cater to different learning styles. This includes interactive modules, engaging videos, real-world case studies, and regular quizzes and assessments to reinforce key concepts. The program should cover a broad spectrum of topics, from recognizing phishing emails and malicious websites to understanding password security best practices and the importance of physical security.
Crucially, the training should be tailored to the specific roles and responsibilities of each employee, ensuring relevance and practicality. Regular refresher courses are vital to keep employees up-to-date with the latest threats and security protocols.
How Effective Training Reduces the Risk of Human Error
Effective cybersecurity awareness training directly mitigates the risk of human error, the leading cause of many security incidents. By educating employees on common attack vectors such as phishing and social engineering, organizations equip them with the knowledge and skills to identify and avoid these threats. Training reinforces safe browsing habits, secure password management, and the importance of reporting suspicious emails or websites.
This proactive approach significantly reduces the likelihood of employees falling victim to attacks, preventing data breaches, malware infections, and other costly security incidents. Regular testing and simulated phishing campaigns can further assess the effectiveness of the training and identify areas for improvement.
Examples of Phishing Scams and Social Engineering Tactics
Attackers employ increasingly sophisticated tactics to deceive unsuspecting individuals. Understanding these tactics is crucial for effective training.
“Urgent: Your account has been compromised. Click here to verify your information immediately: [malicious link]”
This is a classic example of a phishing email attempting to steal login credentials. The urgency and threat of account compromise are designed to pressure the recipient into clicking the malicious link.
“Hello [Employee Name], I’m having trouble accessing the shared drive. Could you please send me your password so I can troubleshoot the issue?”
This illustrates a social engineering attack where the attacker impersonates a colleague to obtain sensitive information. The seemingly innocent request is designed to exploit trust and obtain the password.
“Congratulations! You’ve won a free iPad! Claim your prize by clicking here: [malicious link]”
This example showcases a prize scam, a common type of phishing attack. The promise of a reward entices the recipient to click a link that may contain malware or lead to a fraudulent website.
Investing in Cybersecurity Technologies

In today’s interconnected world, robust cybersecurity is no longer a luxury but a necessity. A proactive approach, involving strategic investment in advanced technologies, is crucial for mitigating the ever-evolving threat landscape. This investment translates directly into protecting sensitive data, maintaining operational continuity, and safeguarding a company’s reputation. The right technology, deployed effectively, provides a layered defense against cyberattacks, minimizing potential damage and financial losses.The effectiveness of a cybersecurity strategy hinges on the careful selection and implementation of appropriate technologies.
A comprehensive approach often involves a combination of solutions, each designed to address specific vulnerabilities and threats. Failing to invest adequately leaves organizations vulnerable to breaches, ransomware attacks, and data loss, resulting in significant financial and reputational damage. The cost of inaction far outweighs the cost of proactive investment.
Firewall Implementation and Management
Firewalls act as the first line of defense, filtering network traffic and blocking unauthorized access. They examine incoming and outgoing network packets based on pre-defined rules, preventing malicious traffic from entering the network. Next-generation firewalls (NGFWs) go beyond basic packet filtering, incorporating advanced features such as deep packet inspection, intrusion prevention, and application control. Effective firewall management includes regular updates, rule optimization, and rigorous monitoring to ensure optimal performance and protection.
For example, a financial institution might use an NGFW with advanced threat intelligence feeds to proactively block known malicious IPs and prevent sophisticated attacks targeting their online banking systems.
Intrusion Detection and Prevention Systems
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) monitor network traffic for suspicious activity, identifying potential threats in real-time. IDS passively monitors and alerts, while IPS actively blocks or mitigates threats. These systems utilize various techniques, including signature-based detection (identifying known attack patterns) and anomaly-based detection (identifying deviations from normal network behavior). A well-configured IPS can prevent a significant number of attacks before they reach their targets.
For instance, a large retail company could deploy an IPS to detect and block Distributed Denial of Service (DDoS) attacks, preventing service disruptions and protecting customer data.
Endpoint Protection Solutions
Endpoint protection encompasses a range of technologies designed to secure individual devices (computers, laptops, mobile devices) connected to a network. These solutions typically include antivirus software, anti-malware, endpoint detection and response (EDR), and data loss prevention (DLP) capabilities. EDR solutions go beyond traditional antivirus by monitoring endpoint activity for malicious behavior, providing advanced threat detection and incident response capabilities.
Consider a healthcare provider implementing EDR to detect and respond to ransomware attacks targeting patient data, preventing a potential HIPAA violation and reputational damage.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities and weaknesses in an organization’s security posture. Security audits involve a systematic review of security policies, procedures, and controls, identifying gaps and areas for improvement. Penetration testing simulates real-world cyberattacks to identify exploitable vulnerabilities. By proactively identifying and addressing weaknesses, organizations can significantly reduce their risk exposure.
For example, a government agency might conduct annual penetration testing to assess the security of its critical infrastructure, ensuring resilience against potential cyber threats. The findings from both audits and penetration tests inform necessary improvements in security technologies and practices.
The Role of Artificial Intelligence in Cybersecurity
The digital landscape is evolving at an unprecedented pace, bringing with it increasingly sophisticated cyber threats. Traditional security measures are often struggling to keep up, creating a critical need for innovative solutions. Artificial intelligence (AI) and machine learning (ML), with their ability to analyze vast amounts of data and identify patterns humans might miss, are emerging as powerful allies in the fight against cybercrime.AI and machine learning are rapidly transforming cybersecurity defenses.
They are being deployed across a range of applications, significantly enhancing our ability to detect, respond to, and prevent cyberattacks. This transformative power stems from AI’s capacity to analyze massive datasets, identify anomalies, and predict potential threats with a speed and accuracy far surpassing human capabilities. This proactive approach allows for faster response times and more effective mitigation strategies.
AI-Powered Threat Detection and Prevention
AI algorithms excel at identifying malicious activities by analyzing network traffic, user behavior, and system logs for anomalies indicative of intrusions or attacks. Machine learning models can be trained on massive datasets of known attacks, enabling them to recognize and flag suspicious patterns in real-time. For instance, an AI system might detect unusual login attempts from unfamiliar geographic locations or identify subtle variations in network traffic that signal a sophisticated attack.
This proactive approach significantly reduces the window of vulnerability and minimizes the impact of successful attacks. Furthermore, AI can adapt to new and evolving threats, constantly learning and refining its detection capabilities. This adaptive learning is crucial in the ever-changing landscape of cybercrime.
AI’s Limitations in Cybersecurity
While AI offers significant advantages, it’s crucial to acknowledge its limitations. AI systems are only as good as the data they are trained on. Biased or incomplete datasets can lead to inaccurate predictions and flawed security measures. Furthermore, sophisticated adversaries are actively developing techniques to evade AI-based detection systems, employing adversarial machine learning to manipulate inputs and circumvent security protocols.
The “black box” nature of some AI algorithms also poses a challenge, making it difficult to understand how they arrive at their conclusions, hindering the debugging process and impacting trust. Finally, the computational resources required to train and deploy sophisticated AI models can be substantial, posing a significant barrier to entry for smaller organizations.
Future Applications of AI in Cybersecurity
The future of AI in cybersecurity is brimming with potential. We can anticipate more sophisticated threat intelligence platforms that leverage AI to predict future attacks based on current trends and vulnerabilities. AI-driven incident response systems will automate the process of identifying and containing breaches, minimizing downtime and damage. Furthermore, AI will play a crucial role in securing emerging technologies like the Internet of Things (IoT) and blockchain, managing the complexities and vulnerabilities inherent in these rapidly expanding ecosystems.
For example, imagine AI systems automatically patching vulnerabilities in IoT devices across a large network, preventing widespread attacks before they even begin. This proactive, automated approach is essential for managing the ever-increasing volume and complexity of connected devices.
Building a Strong Cybersecurity Culture
A robust cybersecurity posture isn’t solely dependent on advanced technologies; it thrives on a culture of security awareness and proactive engagement from every individual within an organization. Building this culture requires a multifaceted approach, embedding security principles into the very fabric of the company’s operations and mindset. This isn’t a one-time project, but an ongoing commitment to continuous improvement and adaptation.A strong cybersecurity culture fosters a shared responsibility for data protection.
It empowers employees at all levels to recognize and report potential threats, transforming them from passive recipients of security policies into active participants in safeguarding sensitive information. This collaborative environment significantly reduces the organization’s vulnerability to cyberattacks and enhances its overall resilience.
Collaboration Between IT Security Teams and Other Departments
Effective cybersecurity requires a holistic approach, transcending the boundaries of the IT security department. Open communication and collaborative efforts between IT security and other departments, such as Human Resources, Legal, and Operations, are crucial. For instance, HR can integrate security awareness training into employee onboarding and ongoing development programs. Legal can ensure compliance with data privacy regulations, while Operations can contribute to implementing robust physical security measures.
This cross-functional collaboration ensures that security considerations are integrated into all aspects of the organization’s operations, minimizing blind spots and maximizing overall security.
Best Practices for Incident Response and Recovery
A well-defined incident response plan is paramount for mitigating the impact of cyberattacks. This plan should Artikel clear procedures for identifying, containing, eradicating, recovering from, and learning from security incidents. Regularly testing and updating this plan is crucial, simulating real-world scenarios to identify weaknesses and refine responses. Key elements of a robust incident response plan include: clearly defined roles and responsibilities, established communication channels, procedures for data backup and recovery, and a process for post-incident analysis and improvement.
For example, a simulated phishing attack can reveal vulnerabilities in employee awareness and highlight areas for improvement in training programs. A detailed post-incident analysis can pinpoint the root cause of a breach, enabling the organization to strengthen its defenses and prevent future incidents. The key is preparation and practice; a well-rehearsed response team can significantly minimize the damage caused by a successful attack.
The journey towards robust cybersecurity is a continuous evolution, demanding constant vigilance and adaptation. While technology provides powerful tools, the human element remains critical. By investing in robust technologies, adhering to stringent regulations, fostering a culture of security awareness, and embracing the potential of AI, we can navigate the ever-changing digital landscape with confidence. The future of our digital world hinges on our collective commitment to prioritizing and strengthening cybersecurity defenses.
It’s not just about protecting data; it’s about protecting our future.
Essential Questionnaire
What is ransomware and how can I protect myself?
Ransomware is malicious software that encrypts your files, making them inaccessible unless you pay a ransom. Protection involves regular backups, strong passwords, updated software, and avoiding suspicious links or attachments.
How can small businesses effectively manage cybersecurity risks?
Small businesses can leverage cloud-based security solutions, implement strong password policies, train employees on phishing awareness, and regularly back up their data. Consider outsourcing some aspects of security management to a specialized firm.
What is the difference between a firewall and an intrusion detection system?
A firewall controls network traffic, blocking unauthorized access. An intrusion detection system monitors network activity for malicious behavior and alerts administrators to potential threats.
What are the legal consequences of a data breach?
Legal consequences vary by jurisdiction but can include hefty fines, lawsuits from affected individuals, reputational damage, and potential criminal charges.
How can I improve my personal cybersecurity hygiene?
Use strong, unique passwords, enable two-factor authentication, be wary of phishing attempts, keep your software updated, and regularly back up your important data.