Imagine a world where your refrigerator orders groceries when supplies run low, your car diagnoses its own mechanical issues, and your doctor remotely monitors your health. This isn’t science fiction; it’s the reality unfolding with the Internet of Things (IoT). This transformative technology connects everyday objects to the internet, creating a network of intelligent devices that communicate and interact with each other and us, revolutionizing industries and reshaping the business landscape.
Prepare to delve into the exciting possibilities and transformative potential of IoT, exploring its core components, diverse applications, and the future it promises.
From smart factories optimizing production to connected healthcare improving patient outcomes, the impact of IoT is undeniable. We’ll examine real-world examples across diverse sectors, uncovering how businesses are leveraging IoT to boost efficiency, enhance customer experiences, and gain a competitive edge. We’ll also navigate the crucial aspects of data security and explore the challenges and opportunities that lie ahead as this technology continues its rapid evolution.
Defining the Internet of Things (IoT)
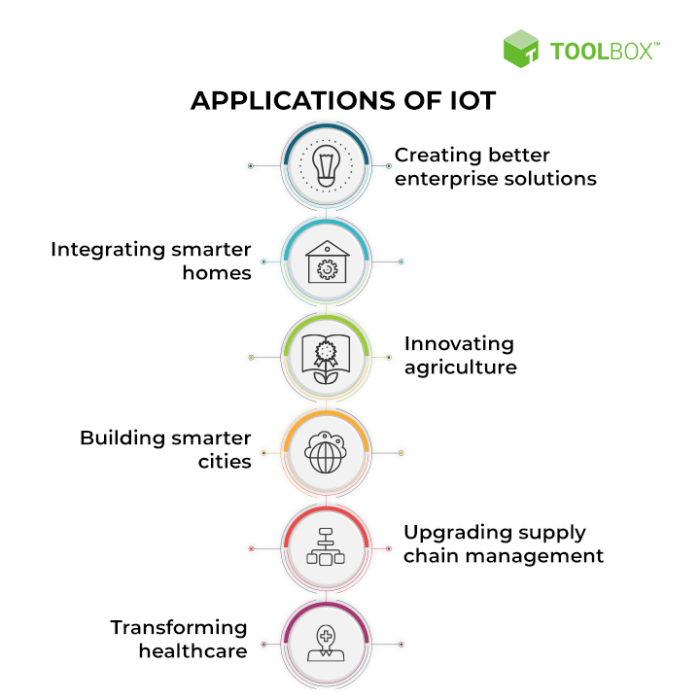
The Internet of Things (IoT) represents a paradigm shift in how we interact with the digital world. It’s a global network of interconnected physical objects, or “things,” embedded with sensors, software, and other technologies for the purpose of exchanging data with other devices and systems over the internet. This interconnectedness enables these objects to collect and exchange data, ultimately automating processes and improving efficiency across a wide range of applications.
The core functionalities revolve around sensing, communication, data processing, and action.The key difference between the IoT and the internet lies in the nature of the connected entities. The internet connects computers and servers, primarily facilitating human-to-human and human-to-machine communication. The IoT, however, connects a vast array of physical objects, enabling machine-to-machine (M2M) communication and interaction. This allows for a level of automation and data-driven decision-making previously unimaginable.
IoT Communication Protocols
Several communication protocols are crucial for enabling seamless data exchange within IoT networks. The choice of protocol often depends on factors such as range, power consumption, bandwidth requirements, and security considerations. Common protocols include:
- MQTT (Message Queuing Telemetry Transport): A lightweight, publish-subscribe protocol ideal for resource-constrained devices and high-volume data transmission. Its efficiency makes it suitable for applications where bandwidth is limited.
- CoAP (Constrained Application Protocol): Designed for constrained environments, CoAP offers a RESTful interface, making it easier to integrate with existing web services. Its simplicity and low overhead make it well-suited for IoT devices with limited processing power.
- HTTP (Hypertext Transfer Protocol): While primarily used for web communication, HTTP can also be utilized in IoT applications, particularly those requiring robust security and well-established infrastructure.
- Bluetooth Low Energy (BLE): A short-range wireless communication technology ideal for connecting nearby devices with low power consumption. BLE is often used in wearable devices and smart home applications.
- Zigbee: A low-power, low-data-rate wireless protocol well-suited for mesh networks. Its ability to create self-healing networks makes it ideal for applications requiring extensive coverage and reliability.
IoT Device Types
IoT networks consist of a diverse range of devices, each playing a specific role in data acquisition and processing.
| Type | Function | Communication Protocol | Example Application |
|---|---|---|---|
| Sensor | Collects data from the physical environment (temperature, pressure, light, etc.) | MQTT, CoAP, BLE | Smart thermostat monitoring room temperature |
| Actuator | Carries out actions based on received data (e.g., turning on/off a light, adjusting a valve) | MQTT, CoAP, Zigbee | Smart sprinkler system adjusting water flow based on soil moisture sensor data |
| Gateway | Connects IoT devices to the internet, aggregating and translating data for transmission to cloud platforms | Ethernet, Wi-Fi, cellular | Connecting a network of smart home devices to a central server for remote monitoring and control |
| Edge Device | Performs data processing and analysis at the network edge, reducing latency and bandwidth requirements | Various, depending on the application | Analyzing sensor data from a manufacturing plant to detect anomalies in real-time |
IoT Business Applications Across Industries
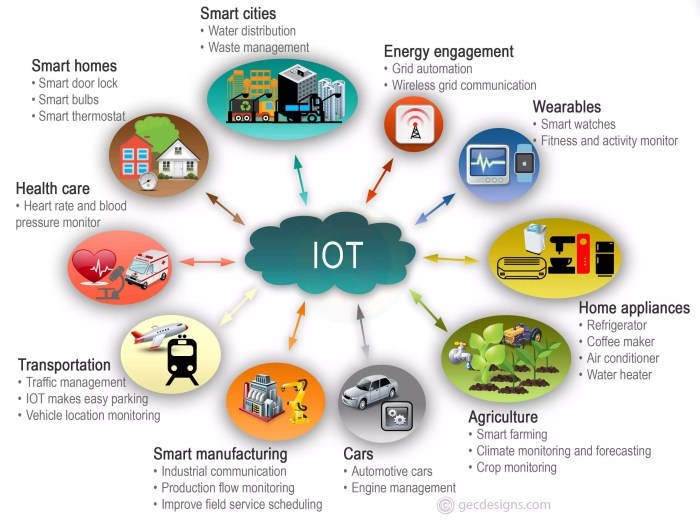
The Internet of Things (IoT) is rapidly transforming industries, creating unprecedented opportunities for efficiency, innovation, and profitability. By connecting devices and systems, IoT unlocks vast amounts of data, enabling businesses to make data-driven decisions, optimize processes, and create entirely new products and services. This section explores the significant impact of IoT across key sectors, highlighting successful implementations and the potential for future disruption.
IoT Applications in Manufacturing
The manufacturing sector is experiencing a profound shift thanks to IoT. Real-time data collection from connected machinery and sensors allows for predictive maintenance, optimized production processes, and enhanced quality control. This leads to reduced downtime, increased output, and significant cost savings.
Successful IoT implementations in manufacturing frequently involve:
- Predictive Maintenance: Sensors monitor equipment performance, predicting potential failures before they occur. This allows for proactive maintenance, minimizing downtime and preventing costly repairs.
- Supply Chain Optimization: Tracking goods and materials throughout the supply chain using RFID tags and other IoT devices improves visibility and efficiency, reducing delays and waste.
- Automated Quality Control: Sensors and cameras integrated into the production line automatically detect defects, ensuring consistent product quality and reducing manual inspection needs.
IoT Applications in Healthcare
IoT is revolutionizing healthcare, improving patient care, streamlining operations, and enhancing overall efficiency. From remote patient monitoring to smart medical devices, IoT technologies are creating a more connected and responsive healthcare ecosystem.
Examples of successful IoT applications in healthcare include:
- Remote Patient Monitoring: Wearable sensors and connected devices track vital signs and other health data, enabling remote monitoring of patients with chronic conditions. This allows for early detection of problems and timely intervention.
- Smart Medical Devices: Implantable devices and connected medical equipment provide real-time data on patient health, facilitating better diagnosis and treatment. This also enhances the accuracy and efficiency of medical procedures.
- Inventory Management: IoT sensors track medical supplies and equipment, ensuring optimal stock levels and preventing shortages. This minimizes disruptions to patient care and reduces waste.
IoT Applications in Retail
The retail industry is leveraging IoT to enhance the customer experience, optimize operations, and gain a competitive edge. From smart shelves to personalized marketing, IoT is transforming how retailers interact with their customers and manage their businesses.
Successful examples of IoT in retail include:
- Smart Shelves: Sensors embedded in shelves track inventory levels, automatically alerting staff when restocking is needed. This minimizes stockouts and ensures products are always available.
- Personalized Marketing: IoT devices collect data on customer behavior and preferences, enabling retailers to deliver personalized marketing messages and promotions. This increases customer engagement and sales.
- Enhanced Security: IoT-enabled security systems monitor store activity, detecting theft and other security breaches. This improves safety and reduces losses.
IoT Disruption of Traditional Business Models
IoT’s potential to disrupt traditional business models is significant. In manufacturing, the shift towards predictive maintenance and automated processes is challenging traditional maintenance schedules and workforce structures. Companies are now investing in data analytics capabilities and upskilling their workforce to manage the influx of data generated by IoT devices. In the healthcare sector, remote patient monitoring is changing the way healthcare is delivered, moving away from traditional clinic-based care towards more proactive and personalized approaches.
This requires new models of care coordination and reimbursement.
Hypothetical IoT Solution for Improved Efficiency in Agriculture
A hypothetical IoT solution for improving efficiency in agriculture could involve a network of sensors deployed across a farm to monitor soil moisture, temperature, light levels, and nutrient levels. This data would be transmitted to a central platform, using a combination of LoRaWAN and cellular networks for reliable long-range communication. The platform would use machine learning algorithms to analyze the data, providing farmers with actionable insights on irrigation needs, fertilization schedules, and pest control strategies.
This precision agriculture approach would optimize resource utilization, minimize waste, and increase crop yields. The system’s components would include soil moisture sensors, temperature and humidity sensors, light sensors, nutrient sensors, a data gateway, a cloud-based platform, and a user-friendly mobile application for farmers to access data and insights. The functionality would encompass real-time monitoring, predictive analytics, automated irrigation control, and alerts for potential issues.
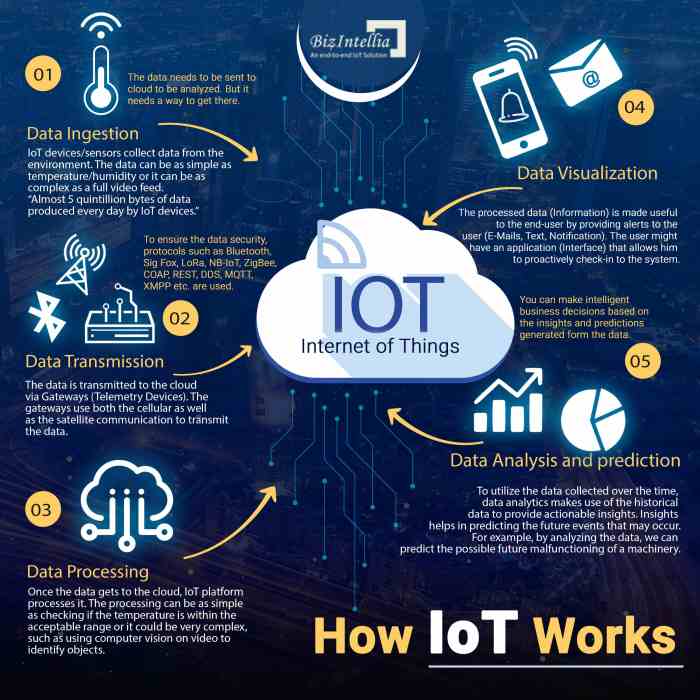
Data Management and Security in IoT
The explosive growth of the Internet of Things (IoT) presents unprecedented opportunities for businesses across diverse sectors. However, this interconnected ecosystem also introduces significant challenges related to data management and security, demanding robust strategies to protect sensitive information and maintain operational integrity. The sheer volume, velocity, and variety of data generated by IoT devices, coupled with their often-limited security capabilities, create a complex security landscape requiring proactive and comprehensive solutions.The interconnected nature of IoT devices and their reliance on cloud-based platforms necessitate a holistic approach to security.
Failing to adequately address these concerns can lead to significant financial losses, reputational damage, and even physical harm. This section will delve into the specific challenges, threats, and mitigation strategies crucial for ensuring the secure and responsible deployment of IoT systems.
Challenges Related to Data Security and Privacy in IoT Deployments
IoT deployments face unique security and privacy challenges stemming from the diverse nature of devices, their often-limited processing power and storage capacity, and the vast amounts of data they generate. Data breaches can expose sensitive personal information, intellectual property, and critical infrastructure controls. Furthermore, the lack of standardized security protocols across different devices and platforms complicates the task of implementing comprehensive security measures.
The decentralized nature of IoT networks also makes it difficult to monitor and control access to data, increasing the risk of unauthorized access and data manipulation. Finally, the increasing reliance on cloud-based platforms for data storage and processing introduces additional vulnerabilities, requiring robust security measures at both the device and cloud levels.
Common Security Threats Associated with IoT Devices and Networks
IoT devices and networks are susceptible to a wide range of security threats. These include unauthorized access, data breaches, denial-of-service attacks, malware infections, and man-in-the-middle attacks. Many IoT devices lack basic security features like strong authentication mechanisms and encryption, making them easy targets for malicious actors. Furthermore, the use of default passwords and lack of regular software updates exacerbate these vulnerabilities.
The sheer number of connected devices in an IoT network also creates a larger attack surface, increasing the likelihood of successful attacks. Compromised IoT devices can be used as part of botnets for launching large-scale attacks, or to gain access to sensitive data within a network. Examples include smart home devices being used to launch DDoS attacks and medical devices being compromised to steal patient data.
Security Measures and Protocols to Mitigate Threats
Implementing robust security measures is paramount for mitigating the risks associated with IoT deployments. This involves a multi-layered approach encompassing device-level security, network security, and data security. Device-level security includes securing firmware, implementing strong authentication mechanisms, and regularly updating software. Network security measures involve securing network infrastructure, implementing firewalls and intrusion detection systems, and using encryption protocols to protect data in transit.
Data security requires secure data storage, access control mechanisms, and data encryption both at rest and in transit. Regular security audits and penetration testing are also crucial to identify and address vulnerabilities before they can be exploited. Employing a zero-trust security model, which assumes no implicit trust, is becoming increasingly important for IoT environments.
Comparison of Data Security Protocols in IoT
The choice of a suitable data security protocol is crucial for ensuring the confidentiality, integrity, and availability of data in IoT deployments. The following table compares three commonly used protocols:
| Protocol Name | Description | Strengths | Weaknesses |
|---|---|---|---|
| Transport Layer Security (TLS) | Provides secure communication over a network by encrypting data in transit. | Widely adopted, provides strong encryption, relatively easy to implement. | Can be computationally expensive for resource-constrained devices, requires significant processing power. |
| Message Queuing Telemetry Transport (MQTT) | A lightweight messaging protocol designed for machine-to-machine (M2M) communication. | Low bandwidth consumption, suitable for resource-constrained devices, efficient for publish-subscribe communication. | Limited security features in basic implementations, requires additional security layers for robust protection. |
| Data Encryption Standard (DES) | A symmetric-key block cipher that encrypts data in blocks of 64 bits. | Relatively simple to implement, fast encryption and decryption. | 56-bit key size is considered insecure by modern standards, vulnerable to brute-force attacks. Generally superseded by AES. |
The Future of IoT and Emerging Trends

The Internet of Things (IoT) is rapidly evolving, driven by technological advancements and a growing demand for interconnected devices and smart solutions across diverse sectors. The future of IoT promises unprecedented levels of automation, efficiency, and data-driven insights, transforming how we live, work, and interact with our environment. This section explores the key trends shaping this transformative landscape.
The Impact of 5G and Edge Computing
G’s significantly increased speed, lower latency, and higher bandwidth capacity will revolutionize IoT by enabling real-time data transmission from a vastly larger number of connected devices. This is particularly crucial for applications requiring immediate responsiveness, such as autonomous vehicles, remote surgery, and industrial automation. Edge computing, processing data closer to the source rather than relying solely on cloud infrastructure, will further enhance IoT performance by reducing latency, improving security, and enabling more efficient data management.
For example, a smart factory utilizing 5G and edge computing can process sensor data from machines in real-time, allowing for immediate adjustments to optimize production and prevent equipment failures, unlike older systems with significant delays.
Emerging Trends in the IoT Landscape
The IoT landscape is constantly evolving, with several key trends shaping its future.
- AIoT (Artificial Intelligence of Things): The integration of AI and ML algorithms into IoT devices and systems is creating intelligent, self-learning networks. AIoT enables predictive maintenance, advanced analytics, and automated decision-making. For instance, smart home devices equipped with AI can learn user preferences and automatically adjust settings for optimal comfort and energy efficiency. This goes beyond simple automation, allowing for personalized experiences and proactive problem-solving.
- Industrial IoT (IIoT): IIoT is transforming manufacturing, logistics, and other industrial sectors through connected sensors, machines, and systems. This leads to improved operational efficiency, predictive maintenance, and enhanced safety. For example, IIoT-enabled smart factories can monitor equipment performance in real-time, predict potential failures, and optimize production schedules, minimizing downtime and maximizing output. Real-world examples include companies like Siemens and GE, which are heavily investing in and implementing IIoT solutions across their industrial operations.
- Blockchain Technology in IoT: Blockchain’s decentralized and secure nature offers a robust solution for data management and security in IoT networks. This is particularly important for applications requiring high levels of trust and transparency, such as supply chain management and healthcare. By recording data immutably on a blockchain, the integrity and authenticity of IoT data can be ensured, enhancing security and preventing tampering or fraud.
For example, tracking pharmaceuticals through a blockchain-enabled IoT system can ensure that products are not counterfeit and have maintained the correct temperature throughout the supply chain.
The Role of AI and Machine Learning in Enhancing IoT Applications
AI and ML are integral to the future of IoT, empowering devices and systems with intelligence and autonomy. ML algorithms can analyze massive datasets generated by IoT devices, identifying patterns, predicting future events, and enabling automated responses. This leads to more efficient resource management, improved decision-making, and enhanced user experiences. For example, AI-powered predictive maintenance in industrial settings can analyze sensor data to anticipate equipment failures, allowing for timely repairs and preventing costly downtime.
Similarly, in smart cities, AI can analyze traffic patterns to optimize traffic flow and reduce congestion.
Visual Representation of IoT Evolution
Imagine a timeline depicting the evolution of IoT. The early stages (circa 2000s) are represented by a few sparsely connected nodes, representing simple devices like smart refrigerators communicating basic information. This represents the nascent stage of IoT, characterized by limited connectivity and functionality. The middle phase (2010s) shows a significantly denser network, with a greater number of devices interconnected and exchanging larger volumes of data.
This represents the growth of IoT with the introduction of smartphones and increased bandwidth. The projected future (2030s and beyond) is depicted as a vast, complex network of interconnected devices, with advanced AI and ML capabilities. The network is highly dynamic and self-managing, with seamless integration across various systems. The nodes are not just simple devices but sophisticated, autonomous agents capable of complex decision-making and interaction.
This visualizes the advanced capabilities of future IoT, including seamless integration with other technologies, advanced analytics, and proactive problem-solving. The transition shows an increase in both the number of devices and the complexity of their interactions, ultimately leading to a highly interconnected and intelligent ecosystem.
IoT Implementation Challenges and Considerations
Successfully integrating Internet of Things (IoT) solutions requires careful planning and execution. Businesses often encounter significant hurdles during implementation, impacting project timelines, budgets, and ultimately, the potential return on investment. Understanding these challenges and proactively addressing them is crucial for a smooth and successful IoT deployment.
Implementing IoT involves more than simply connecting devices. It requires a holistic approach encompassing hardware selection, software integration, data management, security protocols, and ongoing maintenance. Failure to account for these interconnected elements can lead to significant complications and unforeseen expenses.
Interoperability and Standardization in IoT Ecosystems
Interoperability, the ability of different IoT devices and systems to seamlessly communicate and exchange data, is paramount. Without it, an IoT ecosystem becomes a fragmented collection of incompatible components, hindering data analysis and limiting the potential benefits. Standardization, through the adoption of common protocols and data formats, facilitates interoperability and reduces complexity. For example, the lack of standardization in communication protocols can lead to incompatibility between devices from different manufacturers, requiring expensive custom integrations.
The adoption of standards like MQTT (Message Queuing Telemetry Transport) or CoAP (Constrained Application Protocol) significantly improves interoperability and reduces development time and costs.
Cost-Effectiveness and Return on Investment (ROI) in IoT Projects
IoT projects can involve substantial upfront investments in hardware, software, integration, and ongoing maintenance. Careful planning and cost analysis are essential to ensure cost-effectiveness and a positive ROI. Factors to consider include the initial investment costs, ongoing operational expenses (such as cloud storage, network bandwidth, and maintenance contracts), and the potential revenue generated by the IoT solution. A detailed cost-benefit analysis, projecting both short-term and long-term costs and benefits, is crucial for justifying the investment.
For example, a smart agriculture system may require significant investment in sensors, gateways, and data analytics software, but the potential for increased yield and reduced resource consumption can provide a substantial ROI over time.
Comparison of IoT Deployment Models
Choosing the right deployment model is a critical decision impacting cost, scalability, and security. Different models offer distinct advantages and disadvantages.
| Model | Description | Advantages | Disadvantages |
|---|---|---|---|
| Cloud-based | Data and processing are handled by a cloud service provider. | Scalability, cost-effectiveness (reduced upfront infrastructure investment), ease of management. | Data security concerns, dependence on internet connectivity, potential vendor lock-in. |
| On-premise | Data and processing are managed within the organization’s own infrastructure. | Greater control over data security and privacy, no reliance on internet connectivity. | Higher upfront investment, increased operational costs, limited scalability. |
| Hybrid | A combination of cloud-based and on-premise deployments, leveraging the strengths of both. | Flexibility, enhanced security, optimized cost-effectiveness. | Increased complexity in management and integration. |
| Edge Computing | Processing occurs closer to the data source (at the edge of the network), reducing latency and bandwidth requirements. | Reduced latency, improved responsiveness, enhanced security (reduced data transfer). | Increased hardware and software costs at the edge locations, complexity in management of distributed systems. |
The Internet of Things is not merely a technological advancement; it’s a fundamental shift in how we interact with the world around us. Its influence extends far beyond individual convenience, impacting entire industries and reshaping global economies. As we’ve explored, the potential benefits are immense, from increased efficiency and cost savings to enhanced safety and improved decision-making. However, realizing this potential requires careful consideration of security, data privacy, and the strategic implementation of IoT solutions.
Embracing the opportunities while mitigating the risks is key to unlocking the true transformative power of the IoT revolution, ushering in an era of unprecedented connectivity and innovation.
Questions Often Asked
What are the biggest challenges in IoT security?
Major challenges include the sheer number of devices, their varying security levels, and the vulnerability of networks to attacks. Data breaches, unauthorized access, and denial-of-service attacks are significant concerns.
How does IoT impact customer experience?
IoT enhances customer experience through personalized services, proactive support, and improved convenience. For example, smart home devices offer seamless control and retailers use IoT to track inventory and personalize offers.
What is the return on investment (ROI) for IoT projects?
ROI varies widely depending on the specific application and implementation. Potential benefits include reduced operational costs, increased efficiency, new revenue streams, and improved decision-making. Careful planning and clear objectives are crucial for maximizing ROI.
What are some emerging IoT applications we can expect in the near future?
Expect to see growth in areas like smart cities, precision agriculture, industrial automation, and advanced healthcare monitoring, all driven by AI, 5G, and edge computing.
How does IoT differ from the traditional internet?
The traditional internet connects computers and devices primarily for communication and information access. IoT extends this by connecting everyday objects, enabling them to collect data, interact, and automate processes.